What’s frustrating is how many lies were told and how hard it is to address them as a convict. When you accuse the government of fabricating, falsifying and planting evidence, in this case planting hidden files in an encrypted directory that is now somehow unencrypted, everyone rolls their eyes… even though it’s the only explanation.
Fraudulent Indictment
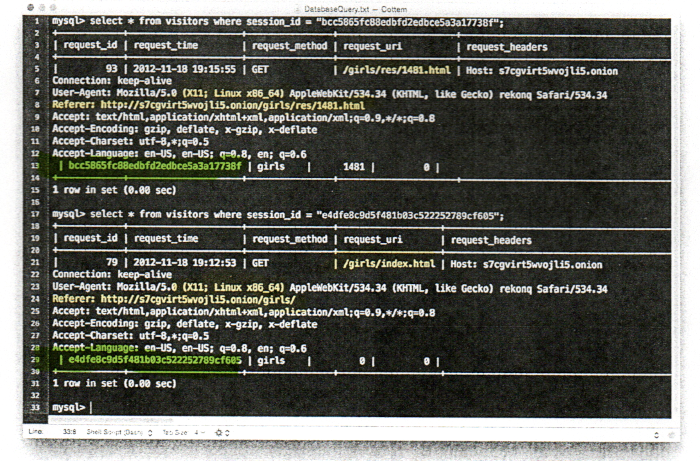
On March 20, 2013, the government obtained a John Doe indictment against Kirk Cottom for visiting a site named TB2 on the TOR network. My petition soon to be before the Eighth Circuit, proves – beyond a reasonable doubt – that the indictment was procured with perjury about fabricated and falsified computer logs.
Planting Evidence
On April 9, 2013, when the FBI showed up at my house, they violated the knock and announce rule. That rule states that they must knock on your door and wait for an answer. When the “target” opens the door they must announce why they’re at your house. In this case, the FBI was required to announce they were at my house to execute a search warrant. Instead, in clear violation of this rule, they knocked and talked. This is the constitutional rule that when the FBI doesn’t have a search warrant they can knock on your door and try to talk you into allowing them to search. So I assumed they were on a knock and talk fishing expedition and talked to them; BUT, when they asked for permission to search, I asked them to leave.
That’s when they revealed that they had a search warrant. I told them they were required to tell me that at my door. They shrugged and told me to take it up with the judge. They then searched my linux computer’s 500GB Operating system drive. After about an hour of finding nothing, they opened my Windows Laptop and found my picture associated with an account named Adama on the Lock Screen. I thought “if these clowns come back in a few minutes claiming to have found something in the Adama account on the linux box I’ll know the fix is in…”
Sure enough, a few minutes later they claim to have found images in Adama’s home directory. I exclaim “bullshit!” For two reasons: 1) The Adama account on the linux box was NEVER used. AND 2) The home directories for all three accounts Kirk, Simon and Adama were encrypted, so it would be impossible to find any files in any of the home directories.
About a year later, I get the forensic report from the FBI and it states that Kirk & Simon are encrypted BUT Adama isn’t. The FBI tech notes that the Adama account is locked by the operating system. I tell my lawyer this is because the FBI over-wrote Adama’s encrypted home directory, when the FBI tech booted the image of the tampered with linux system, it noticed the now unencrypted Adama account and locked it. My lawyer ignored me and no-one besides the FBI tech ever examined the drive.